Forwarding HTTPS on a Zyxel VMG8825-T50 and other configuration shenanigans
Years ago my ISP provided me with a Zyxel VMG8825-T50 modem/router to connect my home network with their ADSL service. I have been using it ever since, and I'd say it is adequate. I guess. It is stable and has the basic functionality I want, although the admin interface looks like it was built and designed 20 years ago. It also has some quirks. But I was able to work around them for all these years.
But then the moment came that I really wanted to... drumroll forward port 443 to a web server I run at home. To be clear, the device supports port forwarding and multiple ports have successfully been forwarded over the years. It all works fine. However, this one, 443, the port for HTTPS, never worked. You could configure it, but a browser would just never get a connection.
Digging around once more, I discovered the culprit. The device has an option to allow external management. That I had turned off. But apparently it still somehow occupied port 443. When I updated the configuration for it to be still turned off, but now on port 444, the HTTPS forwarding magically worked.
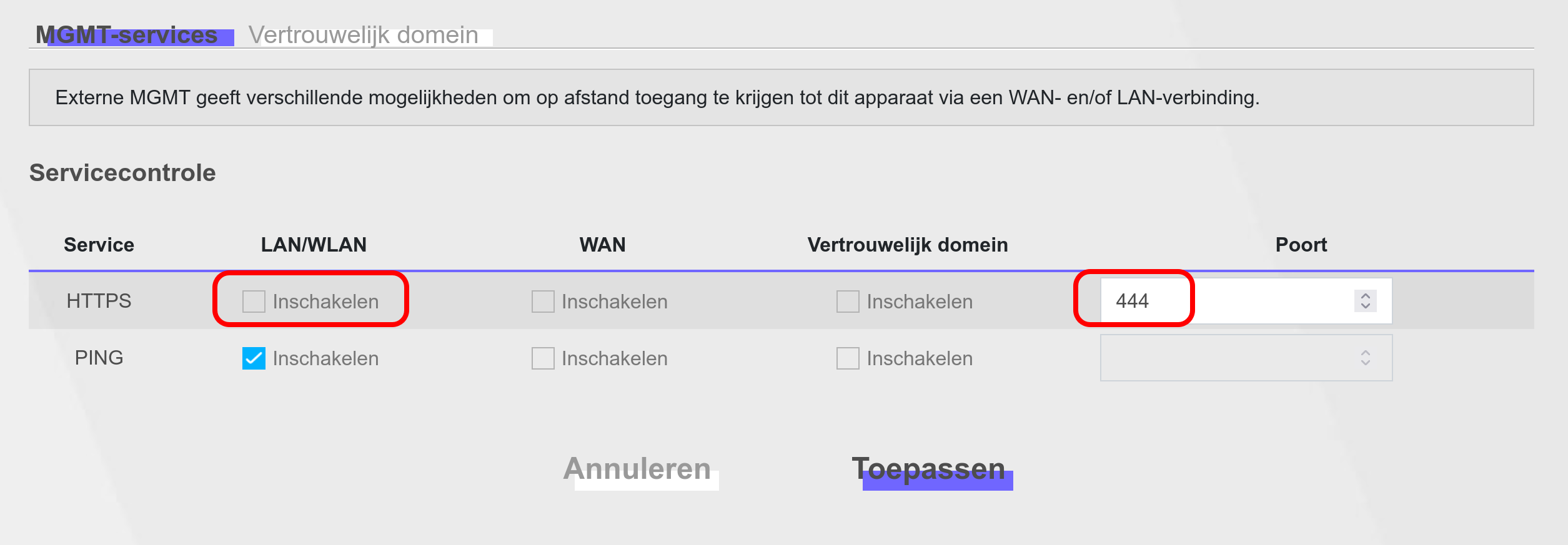
Success!
Or so I thought.
The next day, I wanted to look at the settings again, and I discovered that I was unable to log in at all. See, I normally use plain HTTP for logging in. This is my own network, I am the only user, who cares whether the traffic on it is encrypted? But that was the other quirk I got used to. The interface always tried to redirect the browser to the HTTPS version, which had never worked. Presumably because with the setting described above, all management access got turned off.
This was never a problem, though. The redirect was so slow that I was already done by the time the page refreshed!
This time, however, the redirect happened instantly. And failed. I could see a flash of the log page and then the browser would redirect and report "connection lost".
What to do? On the page is a piece of JavaScript that is very eager to move you to "safe" grounds. Disabling does not work because the whole interface is built with JavaScript. I tried to block the specific redirect call with ad blockers, etc., but no luck.
And then I figured that the script would probably not be very sophisticated. It would likely just look at the protocol, not the host or the whole URL. So I asked an AI to generate a nginx configuration snippet that would let nginx function as an HTTPS proxy with a self-signed certificate:
server {
listen 443 ssl http2 default_server;
listen [::]:443 ssl http2 default_server;
server_name _;
# Self-signed certificate
ssl_certificate /etc/nginx/ssl/nginx-selfsigned.crt;
ssl_certificate_key /etc/nginx/ssl/nginx-selfsigned.key;
# SSL configuration (relaxed for testing)
ssl_protocols TLSv1.2 TLSv1.3;
location / {
set $redirect 0;
# redirect to my home page if someone from outside somehow managed to load this
if ($remote_addr !~ "^(10\.|172\.(1[6-9]|2[0-9]|3[01])\.|192\.168\.)") {
set $redirect 1;
}
if ($redirect = 1) {
return 301 https://ewintr.nl$request_uri;
}
# Proxy to HTTP backend, assuming 192.168.1.1 doesn't support HTTPS
proxy_pass http://192.168.1.1;
proxy_set_header Host $host;
proxy_set_header X-Real-IP $remote_addr;
proxy_set_header X-Forwarded-For $proxy_add_x_forwarded_for;
proxy_set_header X-Forwarded-Proto $scheme;
}
}
Now if I want to access the configuration of my Zyxel:
- Disable the normal default site and enable the one above
- Point browser to
https://[internal IP address of web server]/(The local server that started the need for the whole forwarding configuration in the first place) - Ignore the warning about the self-signed certificate
- Browse the admin interface without any problems.
- Disable this site again.
Success! For real this time.